The SSH2 protocol implemented in OpenSSH is standardized by the IETF secshworking group and is specified in several RFCs and drafts. The overall structure of SSH2 is described in the architectureRFC. It is composed of three layered components.
- 4Procedure
- 4.6Start the sshd Server at Boot
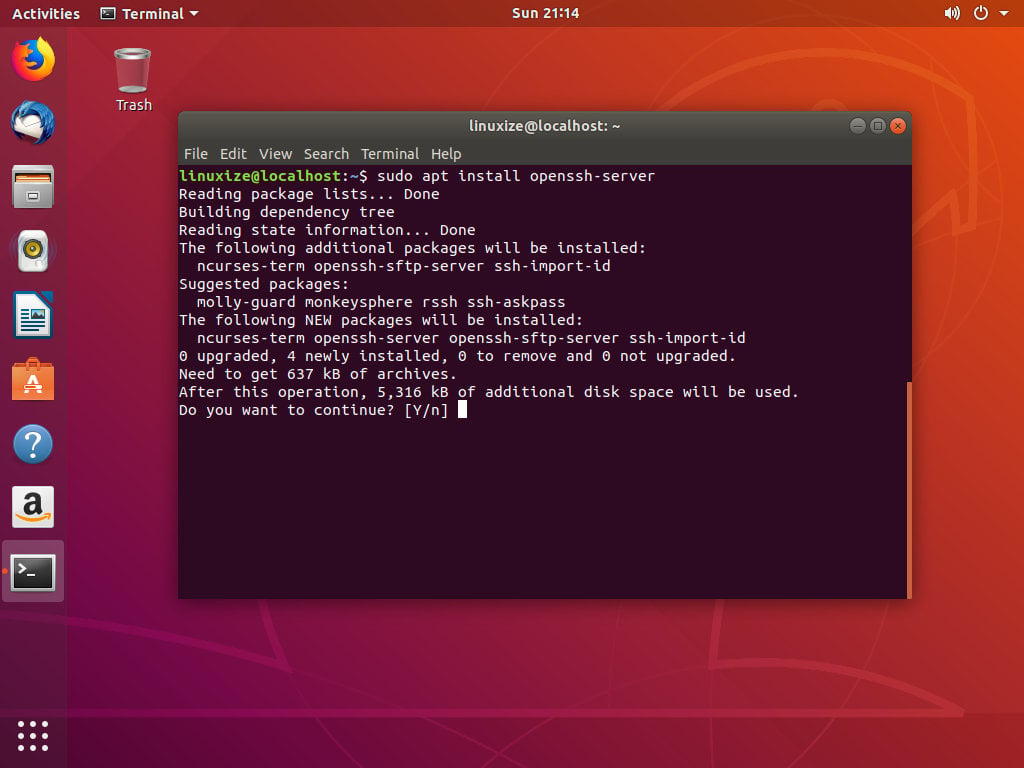
Configuring the default shell for OpenSSH in Windows The default command shell provides the experience a user sees when connecting to the server using SSH. The initial default Windows is the Windows Command shell (cmd.exe). Securing SSH Server. You can secure your OpenSSH server by setting the following options in the sshdconfig configuration file. X11Forwarding – Enabling X forwarding makes your system vulnerable to X11 related issues. So it’s a good idea to set it to no. PermitRootLogin – You should not allow root users to login directly to the system. You should always set it to no. The SSH protocol (aka Secure Shell) is used to establish secure and reliable communications between two hosts. It supports different ssh authentication methods and uses strong encryption to protect exchanged data.It is possible to use SSH-based communications instead of clear-text remote CLI protocols (telnet, rlogin) and unencrypted file transfer methods (such as FTP).
This article contains the procedure to configure a Windows Subsystem for Linux sshd to start at boot and allow ssh access to the Windows host.
Installation
OpenSSH server should be installed by default: /usr/sbin/sshd should exist.
If it is not, download and install the appropriate packages:
UsePrivilegeSeparation
Turn UsePrivilegeSeparation off by setting:

in /etc/ssh/sshd_config.
This is required to prevent sshd startup error that manifests in logs as:
Regenerate Server Keys
Regenerate the server keys following the procedure described here:
- Regenerate Server Keys
This is required to prevent sshd startup error that manifests in the logs as:
Configure User Access
Chiru hits mp3 songs free, download. Add allowed public keys in ~/.ssh/authorized_keys
Set acceptable permissions:
Start the sshd Server
Start the sshd Server at Boot
Passwordless Sudo
Give passwordless sudo privileges the user that is supposed to start the server, by editing the sudo configuration file with visudo. More details: Allow a user to run commands as root without a password.
Windows Startup Script
Create autostartssh.vbs with the following content:
Automatically Execute the Windows Startup Script at Boot
Task Scheduler -> Create Basic Task -> ..
TODO: this did not work, revisit.
Configure the Windows Firewall
- Add a Custom Windows Firewall Rule
I am using a fuse/sshfs mount which worked fine so far. Now I had to reinstall the server system and suddenly getting the classicread: Connection reset by peer error. I am using public key authentication and copied my key to the newly installed system. Normal ssh login works fine. I changed the log to debug but sadly this doesn't give me any useful information:
Does anyone have an idea what I am missing here?
Openssh Ssh-keygen
UPDATE
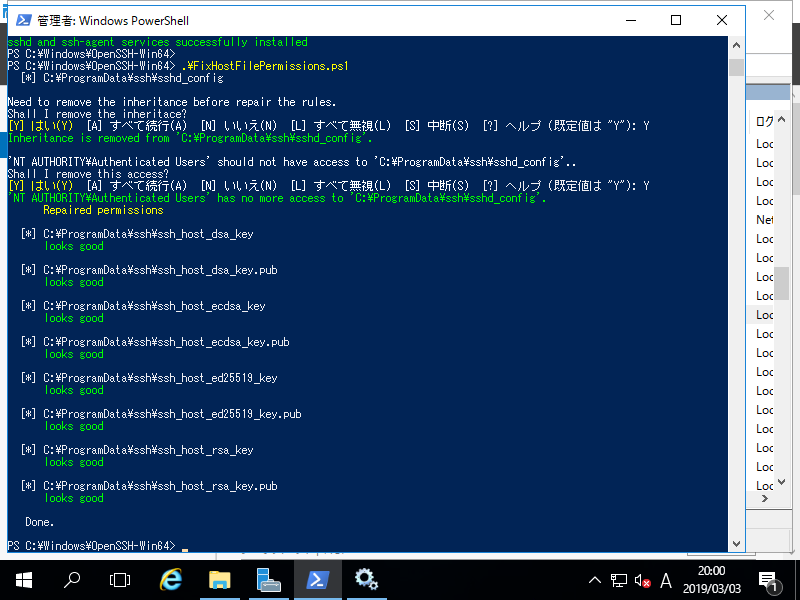
Theauth.log with debug level 3:
UPDATE
I tried a manualsshfs mount and I also get read: Connection reset by peer. I then added the debuging options and also got Permission denied (publickey).. This is strange since the public key is in place and works fine otherwise. I also use my user for the ssh connection and manually specify the private key file. Could this be an issue with the root account not beeing able to access the correct public key on the server somewhere? I'm executing
and the relevant log part is
The output looks exactly like one from a ssh session which refuses to connect due to server key fingerprint mismatch (or an unknown key). Does sftp to the server work correctly? – peterphOct 12 '13 at 8:19 | ||
I tried sftp with both Nautilus (Connect to Server.. option) and Filezilla. It works fine. Although Filezilla asked my about an unknown host key. – André StannekOct 12 '13 at 11:09 | ||
Try sftp directly - that is what SSHFS uses. – peterphOct 12 '13 at 15:23 | ||
| Looks the same to me. Have you tried to get some debugging info from the client? sshfs -odebug,sshfs_debug,loglevel=debug .. could do the trick (taken from sourceforge.net/apps/mediawiki/fuse/index.php?title=SshfsFaq). Green volcanic glass. – peterphOct 12 '13 at 16:54 | |
| @peterph already got that idea ;-) See my second update. I just omitted the debug parameters in the command posted here but I executed it with them. – André StannekOct 12 '13 at 16:57 |
Start Openssh Server
After a lot more of trying it turns out my client user wasn't in the fuse group. After I added it with sudo usermod -a -G fuse myuser the mount works fine again. Don't ask me how it could have worked before reinstalling the server. Thank for all your help!

Openssh Ssh_config
I found my problem, which was similar, had to do with the fuse configuration file in: I m gonna be ready yolanda adams lyrics.
Openssh Sshd_config
I had to un-comment:
